Using SSL securely in your browser
The website How's My SSL shows you, how your Browser handles HTTPS connections. In the case of Firefox 24 it shows:
Your SSL client is Bad.
But how can you improve this? I wrote some hints below:
Firefox
I use Firefox 24. So all I wrote below belongs to this version. Future Firefox versions will bring some improvements. So some settings will be unnecessary then.
All settings must be made by using about:config. The configuration menu is not able to handle it. Enter about:config into the address bar. Firefox prints a warning, that changes will have effects on the security, stability etc. I assume that none of the settings below have negative impact. Thatswhy I confirmed it and came to the next window.
The config window has a search bar and a listing of configuration settings. Enter tls.v (or tls.version) into the search bar. Now you see four or five results. The important options are security.tls.version.min and security.tls.version.max. Both lines have an integer value in the last column. Those can be 0 (SSL 3.0), 1 (TLS 1.0), 2 (TLS 1.1) or 3 (TLS 1.2). You can change them by double clicking on it. I'd change the value security.tls.version.min to at least 1 (better 2)and security.tls.version.max to 3. If you change the first value to 2, it might be, that some pages don't work anymore. This is because they use some older protocol. However the minimum value should be 1 which is TLS version 1.0. You should contact the administrator of those pages and recommend to change to a newer TLS version. I'd like to hear which sites are affected.
Firefox also uses some insecure cipher suites. So i.a. is the cipher SSL_RSA_FIPS_WITH_3DES_EDE_CBC_SHA supported. To change it, enter fips into the about:config search bar. You should see one result. By double-clicking you can set it to False. Brian Smith pointed out that SSL_RSA_FIPS_WITH_3DES_EDE_CBC_SHA is not insecure. In his pull request at Github he describes why it is the case.
When you reload the HowsMySSL-page, you'd see a new result:
Your SSL client is Probably Okay.
Furthermore I usually deactivate all RC4 cipher suites. I look for rc4 and set them all to False
The Twitter user @andiheimann commented, that the Tor Browser Bundle fails:
@qbi @netzpolitik Der #TorBrwoser fällt beim Test leider auch durch..
— andi (@andiheimann) 10. Januar 2014
Tor has to balance anonymity and security. With those settings the anonymity set reduces and there might be some risks to the anonymity of a Tor user. Thatswhy it is probably better to wait for the new Firefox version.
The Tor Project released version 4 of the Tor Browser Bundle. This version comes with Firefox 31 ESR and disables SSLv3.
Google Chrome and Chromium
 Chrome and Chromium doing a good job by default. Only when you want to disable RC4, you have to call both with specific command line options:
Chrome and Chromium doing a good job by default. Only when you want to disable RC4, you have to call both with specific command line options:
In October 2014 Google announced the POODLE exploit. So you should use at least TLS 1.0 in your browser. This option does exactly this: --ssl-version-min=tls1.
Opera
When using Opera 12 with the SSL-test-site it shows bad results. The recent Windows version 18 as well as Opera Next 19 are shown as »good«. If you see bad result then type Ctrl+F12 to open the settings and navigate to »Advanced« --> »Security« --> »Security Protocols«. You should make sure, that only TLS 1.1 and 1.2 is enabled. In the detail view you'll see all supported ciphers. Disable all ARC4-based ciphers.
A reload shows Opera as Improvable. This is caused by SSL Session Tickets. Unfortunately I found no settings. If you know where to find them, please leave a message.
Safari
Apple's Browser is like Opera: Improvable. Also SSL Session Tickets downgrade the result. As said before, if you know where to change it, please leave a message in the comment section.
Internet Explorer
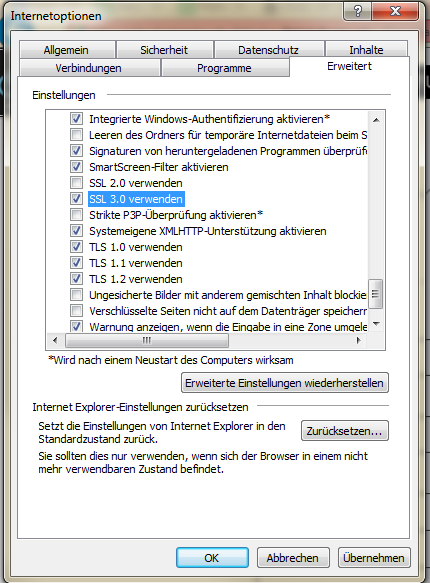
Internet Explorer comes with support for SSLv3. To disable it, go to Internet Options and select the Advanced tab. Near the bottom you'll find a checkbox for using SSLv3. Uncheck and save it. You're done. ![]()
Others
I'll add more browsers later.
Updates:
- Thanks to Brian for his comments on SSL_RSA_FIPS_WITH_3DES_EDE_CBC_SHA and morphium for his comment on Opera
- Recommended TLS 1.0 in Chrome because POODLE.
- Mention that Tor Browser 4 comes without SSLv3.
- Added info about IE